Offered By: IBM
Securing Java microservices with Eclipse MicroProfile JSON W
You’ll explore how to control user and role access to microservices with MicroProfile JSON Web Token (MicroProfile JWT).
Continue readingGuided Project
Open Liberty
66 EnrolledAt a Glance
You’ll explore how to control user and role access to microservices with MicroProfile JSON Web Token (MicroProfile JWT).
You will add token-based authentication mechanisms to authenticate, authorize, and verify users by implementing MicroProfile JWT in the system microservice.
A JSON Web Token (JWT) is a self-contained token that is designed to securely transmit information as a JSON object. The information in this JSON object is digitally signed and can be trusted and verified by the recipient.
For microservices, a token-based authentication mechanism offers a lightweight way for security controls and security tokens to propagate user identities across different services. JSON Web Token is becoming the most common token format because it follows well-defined and known standards.
MicroProfile JWT standards define the required format of JWT for authentication and authorization. The standards also map JWT claims to various Jakarta EE container APIs and make the set of claims available through getter methods.
In this guide, the application uses JWTs to authenticate a user, allowing them to make authorized requests to a secure backend service.
You will be working with two services, a frontend service and a secure system backend service. The frontend service logs a user in, builds a JWT, and makes authorized requests to the secure system service for JVM system properties. The following diagram depicts the application that is used in this guide:
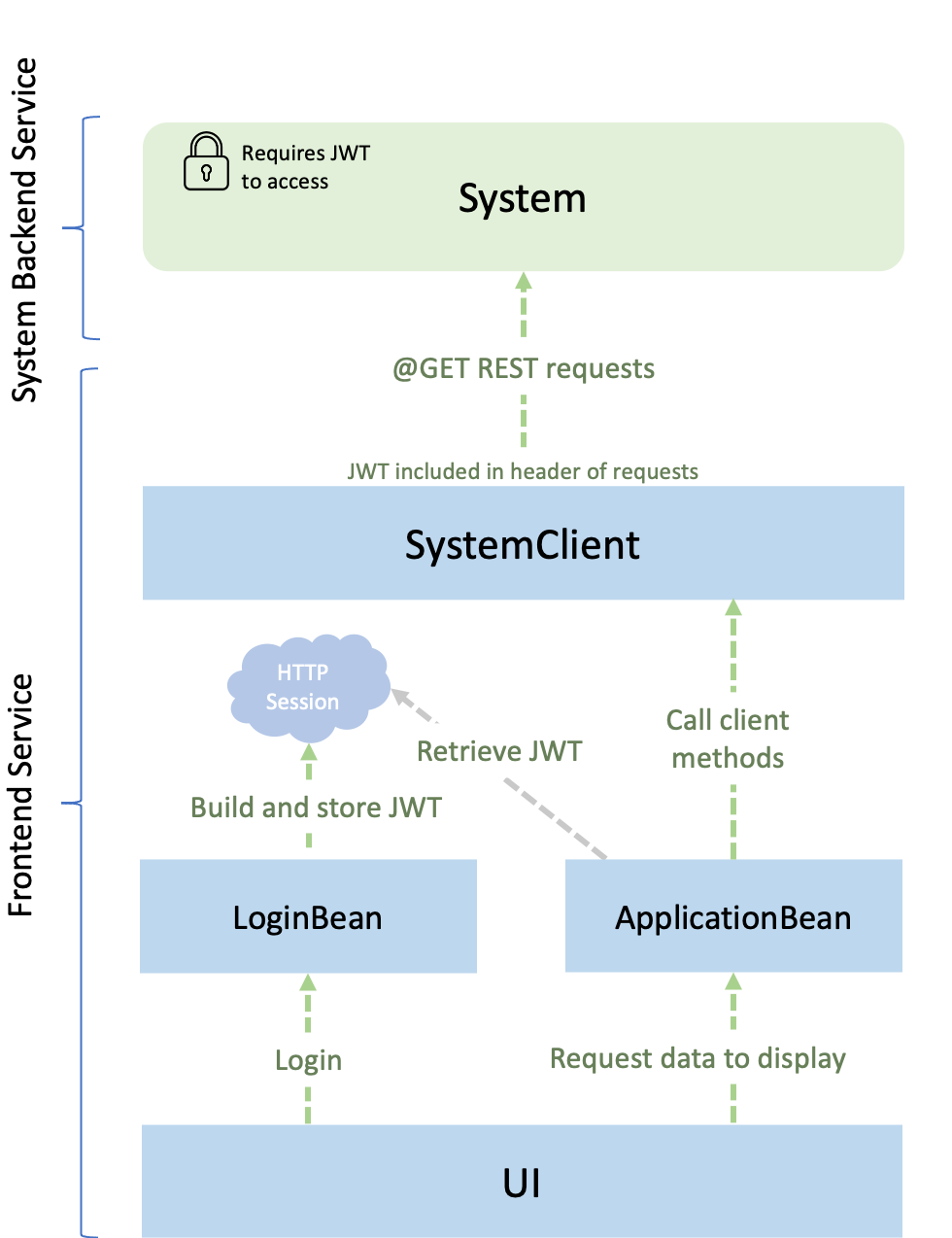

The user signs in to the frontend service with a username and a password, at which point a JWT is created. The frontend service then makes requests, with the JWT included, to the system backend service. The secure system service verifies the JWT to ensure that the request came from the authorized frontend service. After the JWT is validated, the information in the claims, such as the user’s role, can be trusted and used to determine which system properties the user has access to.
To learn more about JSON Web Tokens, check out the jwt.io website. If you want to learn more about how JWTs can be used for user authentication and authorization, check out the Open Liberty Single Sign-on documentation.
Created by
The Open Liberty Project team
Estimated Effort
25 Minutes
Level
Intermediate
Skills You Will Learn
Jakarta EE, MicroProfile, Open Liberty
Language
English
Course Code
GPXX0W7KEN